- As far as I know, all existing images of the Dorabella cipher do not show Elgar's original message, but Penny's rewritten version, which she published in her memoirs. Perhaps this act of rewriting removed some information that might have been helpful. For example: the orientation of the symbols; the length of the lines; since a horizontally reversed symbol is also a valid symbol, perhaps she wrote everything upside down; sometimes the cipher symbols are ambiguous, did she get the right direction of each symbol? etc...
- Elgar used his cipher symbols at least four times: Lisz-Fragment, Courage Card set, Dorabella cipher, notebook.
- The suggested solution(s) for each of these parts do not fit together, i.e., a solutions for the Lisz fragment can not directly be applied to the, e.g., dorabella cipher.
- This either means that those solutions are wrong, or that Elgar slightly varies his system each time, or that Elgar just uses his symbols as a replacement for the alphabet and executes each time a different encryption method, and those do not have anything in common except these symbols.
- The only more or less convincing solution is the one from Tim Roberts, but which has shortcomings in its explanation how Elgar derived the mapping from a letter to a cipher symbol.
- The last usage of his symbols was 23 years after he wrote the Dorabella cipher. In his notebook he wrote several possible orderings of his cipher symbols and also encrypted a few words. Figure 1 shows again this notebook page.
One additional thing he does on this page is, that he writes the sentence "DO YOU GO TO LONDON TOMORROW" on the left side and counts the number of the occurrences of the letter "O". Is the related to his encryption method?
 |
| Figure 1. Elgars notebook. |
A simple assumption. If we assume that he indeed used a similar alphabet to cipher symbol mapping as shown in the notebook, whereby "similar" means: three consecutive letters from the alphabet are always mapped to three equal oriented cipher symbols with an increasing number of cusps.
In that case, you could build up matrix, from which you could potentially eyeball a solution. This assumption is not totally unrealistic but its too simple and if it would be true, such a mapping would probably already have been found. But it is an easy to use improvement to test substitutions for someone who does not want to spend much time in coding.
Nevertheless, i want to present this method shortly, therewith you understand the excel file i want to share with you.
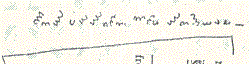 |
| Figure 2. Lisz-Fragment |
We adopt the usual notation, that each cipher symbol is associated with the integer $xy$, whereof $x$ stands for the number of cusps and $y$ is the orientation, that is $1$ is up, going clockwise until $8$, which is upper-left.
Using this particular arrangement from (*), (**) and (***), one could build the following matrix:
\begin{array}{c|c|c|c|c|c|c|c|c|c|c|c|c|c|c|c|c|c}
1&2&3&4&5&6&7&8&9&10&11&12&13&14&15&16&17&18\\
& & & & &3& &1&2& & &4&3&2& & & & \\
44&35&48&21&38&48&25&44&35&45&34&21&48&35&46&31&28&22\\
\hline
C&B&C&A&B&C&A&C&B&C&B&B&A&C&B&C&B&A\\
F&E&F&D&E&F&D&F&E&F&E&E&D&F&E&F&E&D\\
I&H&I&G&H&I&G&I&H&I&H&H&G&I&H&I&H&G\\
M&L&M&K&L&M&K&M&L&M&L&L&K&M&L&M&L&K\\
P&O&P&N&O&P&N&P&O&P&O&O&N&P&O&P&O&N\\
S&R&S&Q&R&S&Q&S&R&S&R&R&Q&S&R&S&R&Q\\
W&U&W&T&U&W&T&W&U&W&U&U&T&W&U&W&U&T\\
Z&Y&Z&X&Y&Z&X&Z&Y&Z&Y&Y&X&Z&Y&Z&Y&X\\
\end{array}
The first line numbers each column, the second line indicates if the cipher symbol is equal to a previous one. That means, those columns depend on the previous choice and must be skipped.
We start at column one and try to build a word or sentence by going from column to column and hoping from row to row. In each dependent row (gray), the same letter must be used as in the previous column with the same cipher symbol. You can not use a letter twice if the cipher symbols are different. I.e. the beginning "I L I K E" is not possible, since in column $1$ and $3$ the $I$ is picked, but the cipher symbols differ.
I wrote a little excel sheet, which you can DOWNLOAD, that does all this for you. It fills the depend columns and removes already chosen letter from the columns if they were picked previously. If you can not find a proper sentence, you can vary the columns by changing the association between the letter set and the cusps symbols shown in (*), (**) and (***).

No comments:
Post a Comment